This guide shows the procedures for setting up to manage Windows Server with Ansible on the targets.
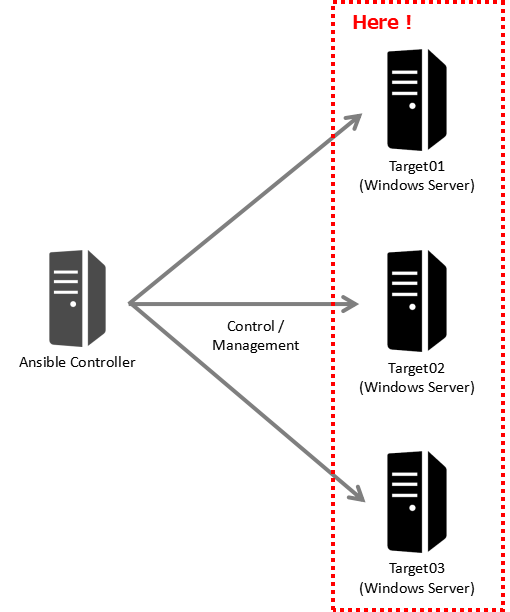
Set up on targets so that Ansible Controller can connect to targets (Windows Server) by WinRM.
The Scope is the following:
- Windows Server 2022
- Windows Server 2019
- Windows Server 2016
Note: About setting up on the Ansible Controller is the following post.
>> Ansible: Setting up to manage Windows
Procedures
Create a WinRM listener on each Windows Server.
Now, run on the PowerShell prompt.
1 (a). For using self-signed certificate
Create a self-signed certificate.
$cert = New-SelfSignedCertificate -DnsName $ENV:COMPUTERNAME -CertStoreLocation Cert:LocalMachine\My-DnsName $ENV:COMPUTERNAME
Set the subject alternative name computer name.
-CertStoreLocation Cert:LocalMachine\My
Create a certificate in the “Local Computer\Personal” store.
1 (b). For using stored certificate
Get a certificate.
$subject = "CN=" + $ENV:COMPUTERNAME$cert = Get-ChildItem -Path "cert:LocalMachine\My" | Where-Object{$_.Subject -eq $subject}This is an example for using a certificate (CN=<computer name>) stored in Local Computer\Personal.
After this you will create WinRM listener by New-WSManInstance cmdlet, but this cmdlet can create a listener with a certificate stored in only Personal.
For that reason if you want to use a certificate stored in other than “Personal” such as Trusted Root Certification Authorities, you have to export and import to Local Computer\Personal.
2. Start WinRM service
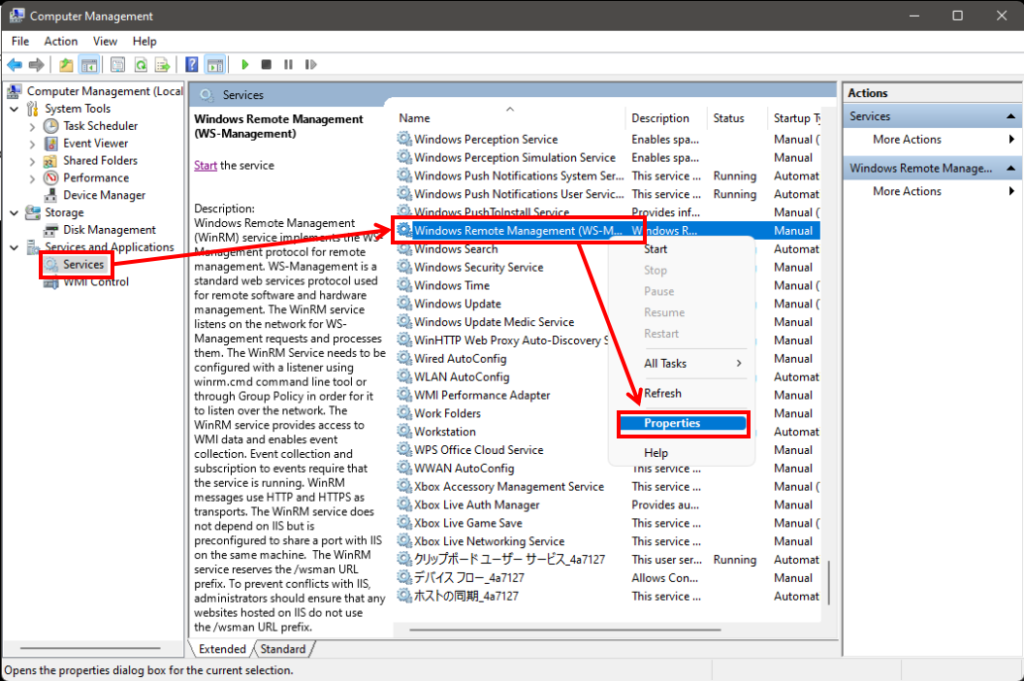
(1) On the Computer Management, select Computer Management > Services and Applications > Services, right-click Windows Remote Management (WS-Management) and click Properties.
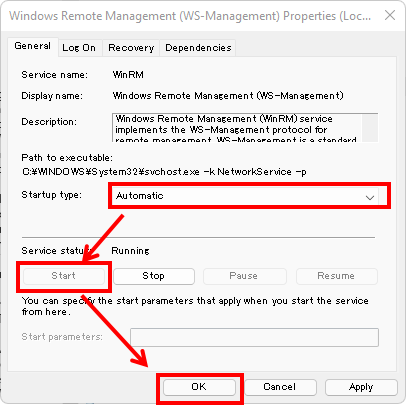
(2) On the Windows Remote Management (WS-Management) Properties, on the General tab, select Automatic at Startup type, click Start and OK.
3. Create Listener
Create WinRM listener.
$selector_set = @{Address="*"; Transport="HTTPS"}$value_set = @{CertificateThumbprint=$cert.Thumbprint}New-WSManInstance -ResourceURI "winrm/config/Listener" -SelectorSet $selector_set -ValueSet $value_setIf it shows like the following, created successfully.
wxf : http://schemas.xmlsoap.org/ws/2004/09/transfer
a : http://schemas.xmlsoap.org/ws/2004/08/addressing
w : http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd
lang : ja-JP
Address : http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous
ReferenceParameters : ReferenceParameters4. Confirm the created listener
To confirm the created listener, run the following command.
winrm enumerate winrm/config/ListenerIf it shows Transport=HTTPSのListener like the following, created successfully.
Listener
Address = *
Transport = HTTPS
Port = 5986
Hostname
Enabled = true
URLPrefix = wsman
CertificateThumbprint = <Thumbprint of certificate>
ListeningOn = 127.0.0.1, <IPv4 address using WinRM>, ::1, <IPv6 address using WinRM>5. Edit options of listener
(1) Edit options of listener.
- Disable Basic Authentication
Set-Item -Path WSMan:\localhost\Service\Auth\Basic -Value false- Enable CredSSP
Enable-WSManCredSSP -role server -Force(2) To get current options, run the following command.
winrm get winrm/config/ServiceCheck options.
Service
RootSDDL = O:NSG:BAD:P(A;;GA;;;BA)(A;;GR;;;IU)S:P(AU;FA;GA;;;WD)(AU;SA;GXGW;;;WD)
MaxConcurrentOperations = 4294967295
MaxConcurrentOperationsPerUser = 1500
EnumerationTimeoutms = 240000
MaxConnections = 300
MaxPacketRetrievalTimeSeconds = 120
AllowUnencrypted = false
Auth
Basic = false
Kerberos = true
Negotiate = true
Certificate = false
CredSSP = true
CbtHardeningLevel = Relaxed
DefaultPorts
HTTP = 5985
HTTPS = 5986
IPv4Filter = *
IPv6Filter = *
EnableCompatibilityHttpListener = false
EnableCompatibilityHttpsListener = false
CertificateThumbprint
AllowRemoteAccess = true4. Edit Windows Firewall
Create an Inbound port (5986/tcp) rule of Windows Firewall.
New-NetFirewallRule -DisplayName "Winrm (SSL)" -Name "WinRM (SSL)" -Profile Any -LocalPort 5986 -Protocol TCPIf it shows like the following, created successfully.
Name : WinRM (SSL)
DisplayName : Winrm (SSL)
Description :
DisplayGroup :
Group :
Enabled : True
Profile : Any
Platform : {}
Direction : Inbound
Action : Allow
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : NotApplicable
PolicyStoreSource : PersistentStore
PolicyStoreSourceType : Local5. Confirm the connection
Connect to myself by WinRM (SSL)
$httpsOptions = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheckNew-PSSession -UseSSL -ComputerName "localhost" -SessionOption $httpsOptions -ErrorVariable httpsError -ErrorAction SilentlyContinueIf it shows like the following, connected successfully.
Id Name ComputerName ComputerType State ConfigurationName Availability
-- ---- ------------ ------------ ----- ----------------- ------------
1 WinRM1 localhost RemoteMachine Opened Microsoft.PowerShell AvailableOn the Windows Server targets, that’s about it.
For deleting WinRM listener
If you want to delete a WinRM listener and self-signed certificate created according to the foregoing procedures, run the following procedures.
(1) Delete lister.
Get-ChildItem -Path WSMan:\localhost\Listener | Where-Object { $_.Keys -contains "Transport=HTTPS" } | Remove-Item -Recurse -Force(2) Confirm deletion.
winrm enumerate winrm/config/ListenerMake sure no listener shows Transport=HTTPS.
(3) Delete a certificate.
$target_store = Get-Item "Cert:LocalMachine\My"$target_cert = (Get-ChildItem "Cert:LocalMachine\My" | ? {$_.Subject -eq "CN=${ENV:COMPUTERNAME}";})$target_store.Open("ReadWrite")$target_store.Remove($target_cert)$target_store.Close()
